AI tools for vulnerability scanning and penetration testing
Related Tools:
OpenBuckets
OpenBuckets is a web application designed to help users find and secure open buckets in cloud storage systems. It provides a simple and efficient way to identify and protect sensitive data that may be exposed due to misconfigured cloud storage settings. With OpenBuckets, users can easily scan their cloud storage accounts for publicly accessible buckets and take necessary actions to safeguard their information.
PixieBrix
PixieBrix is an AI engagement platform that allows users to build, deploy, and manage internal AI tools to drive team productivity. It unifies AI landscapes with oversight and governance for enterprise scale. The platform is enterprise-ready and fully customizable to meet unique needs, and can be deployed on any site, making it easy to integrate into existing systems. PixieBrix leverages the power of AI and automation to harness the latest technology to streamline workflows and take productivity to new heights.
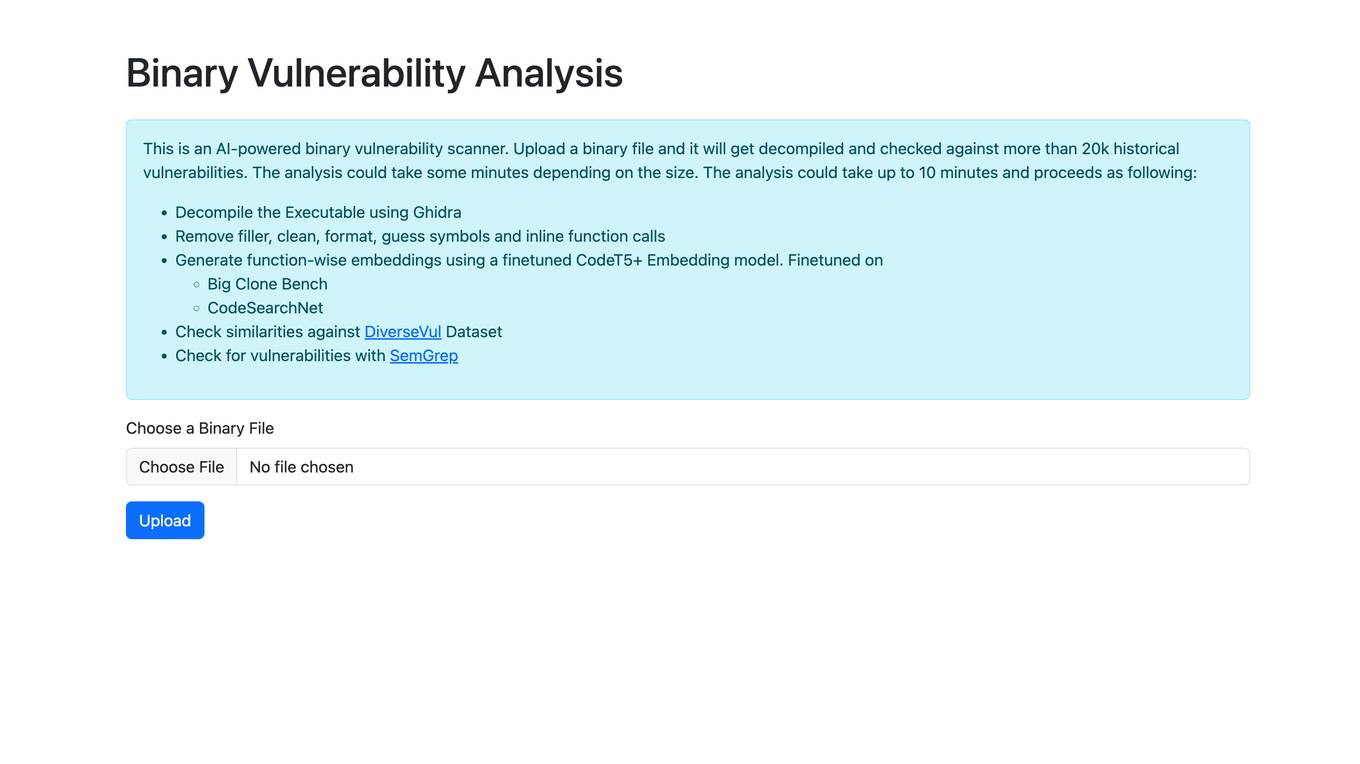
Binary Vulnerability Analysis
The website offers an AI-powered binary vulnerability scanner that allows users to upload a binary file for analysis. The tool decompiles the executable, removes filler, cleans, formats, and checks for historical vulnerabilities. It generates function-wise embeddings using a finetuned CodeT5+ Embedding model and checks for similarities against the DiverseVul Dataset. The tool also utilizes SemGrep to check for vulnerabilities in the binary file.
AquilaX
AquilaX is an AI-powered DevSecOps platform that simplifies security and accelerates development processes. It offers a comprehensive suite of security scanning tools, including secret identification, PII scanning, SAST, container scanning, and more. AquilaX is designed to integrate seamlessly into the development workflow, providing fast and accurate results by leveraging AI models trained on extensive datasets. The platform prioritizes developer experience by eliminating noise and false positives, making it a go-to choice for modern Secure-SDLC teams worldwide.
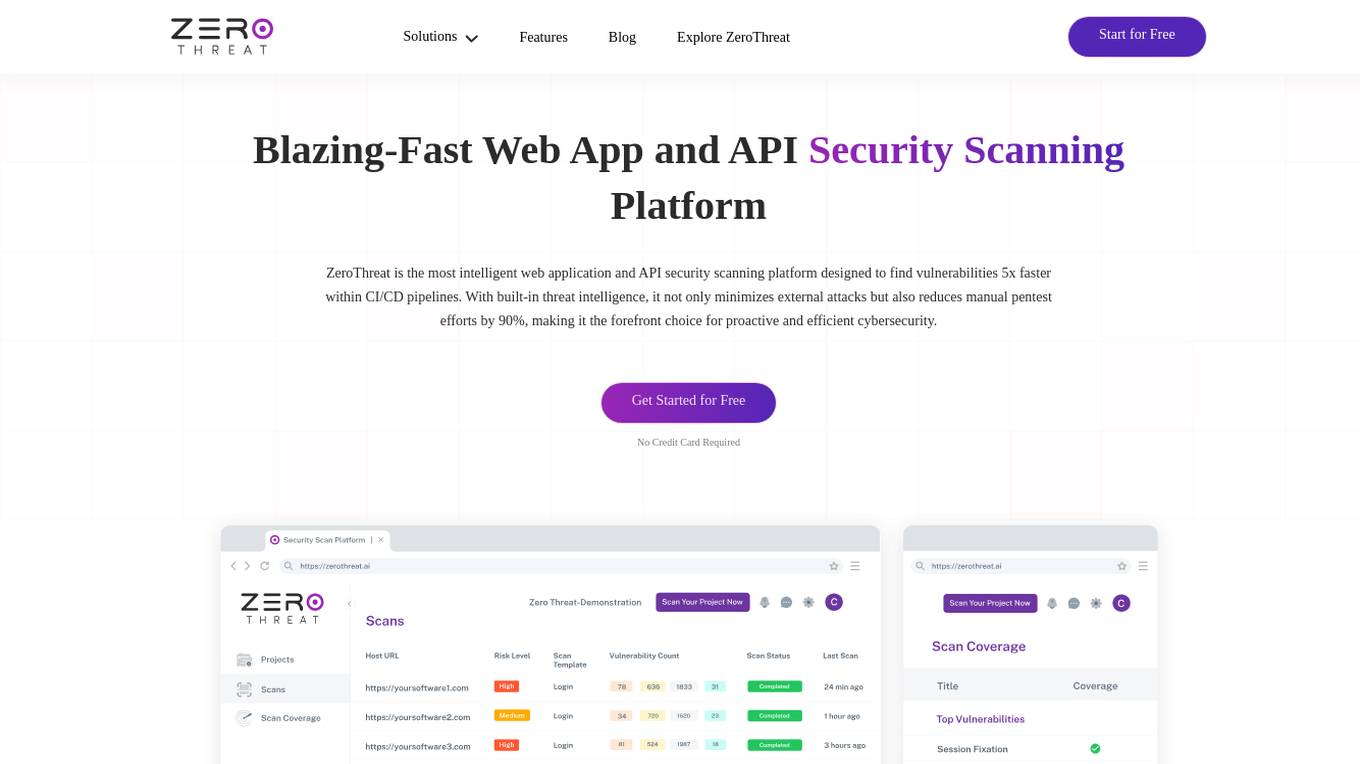
ZeroThreat
ZeroThreat is a web app and API security scanner that helps businesses identify and fix vulnerabilities in their web applications and APIs. It uses a combination of static and dynamic analysis techniques to scan for a wide range of vulnerabilities, including OWASP Top 10, CWE Top 25, and SANS Top 25. ZeroThreat also provides continuous monitoring and alerting, so businesses can stay on top of new vulnerabilities as they emerge.
DepsHub
DepsHub is an AI-powered tool designed to simplify dependency updates for software development teams. It offers automatic dependency updates, license checks, and security vulnerability scanning to ensure teams stay secure and up-to-date. With noise-free dependency management, cross-repository overview, license compliance, and security alerts, DepsHub streamlines the process of managing dependencies for teams of any size. The AI-powered engine analyzes library changelogs, release notes, and codebases to automatically update dependencies, including handling breaking changes. DepsHub supports a wide range of languages and frameworks, making it easy for teams to integrate with their favorite technologies and save time by focusing on writing code that matters.
SANS AI Cybersecurity Hackathon
SANS AI Cybersecurity Hackathon is a global virtual competition that challenges participants to design and build AI-driven solutions to secure systems, protect data, and counter emerging cyber threats. The hackathon offers a platform for cybersecurity professionals and students to showcase their creativity and technical expertise, connect with a global community, and make a real-world impact through AI innovation. Participants are required to create open-source solutions addressing pressing cybersecurity challenges by integrating AI, with a focus on areas like threat detection, incident response, vulnerability scanning, security dashboards, digital forensics, and more.
Cyble
Cyble is a leading threat intelligence platform offering products and services recognized by top industry analysts. It provides AI-driven cyber threat intelligence solutions for enterprises, governments, and individuals. Cyble's offerings include attack surface management, brand intelligence, dark web monitoring, vulnerability management, takedown and disruption services, third-party risk management, incident management, and more. The platform leverages cutting-edge AI technology to enhance cybersecurity efforts and stay ahead of cyber adversaries.
ODIN
ODIN is a powerful internet scanning search engine designed for scanning and cataloging internet assets. It offers enhanced scanning capabilities, faster refresh rates, and comprehensive visibility into open ports. With over 45 modules covering various aspects like HTTP, Elasticsearch, and Redis, ODIN enriches data and provides accurate and up-to-date information. The application uses AI/ML algorithms to detect exposed buckets, files, and potential vulnerabilities. Users can perform granular searches, access exploit information, and integrate effortlessly with ODIN's API, SDKs, and CLI. ODIN allows users to search for hosts, exposed buckets, exposed files, and subdomains, providing detailed insights and supporting diverse threat intelligence applications.
RoostGPT
RoostGPT is an AI-driven testing copilot that offers automated test case generation using Large Language Models (LLMs). It helps in building reliable software by providing 100% test coverage every single time. RoostGPT leverages generative AI to automate test case generation, freeing up developer time and enhancing test accuracy and coverage. It also detects static vulnerabilities in artifacts like source code and logs to ensure data security. The platform is trusted by global financial institutions and industry leaders for its ability to fill gaps in test coverage and simplify testing and deployment processes.
Semgrep
Semgrep is an AI-powered application designed for static analysis and security testing of code. It helps developers find and fix issues in their code, detect vulnerabilities in the software supply chain, and identify hardcoded secrets. Semgrep offers features such as AI-powered noise filtering, dataflow analysis, and tailored remediation guidance. It is known for its speed, transparency, and extensibility, making it a valuable tool for AppSec teams of all sizes.
Qwiet AI
Qwiet AI is a code vulnerability detection platform that accelerates secure coding by uncovering, prioritizing, and generating fixes for top vulnerabilities with a single scan. It offers features such as AI-enhanced SAST, contextual SCA, AI AutoFix, Container Security, SBOM, and Secrets detection. Qwiet AI helps InfoSec teams in companies to accurately pinpoint and autofix risks in their code, reducing false positives and remediation time. The platform provides a unified vulnerability dashboard, prioritizes risks, and offers tailored fix suggestions based on the full context of the code.

Kindo
Kindo is an AI-powered platform designed for DevSecOps teams to automate tasks, write doctrine, and orchestrate infrastructure responses. It offers AI-powered Runbook automations to streamline workflows, automate tedious tasks, and enhance security controls. Kindo enables users to offload time-consuming tasks to AI Agents, prioritize critical tasks, and monitor AI-related activities for compliance and informed decision-making. The platform provides a comprehensive vantage point for modern infrastructure defense and instrumentation, allowing users to create repeatable processes, automate vulnerability assessment and remediation, and secure multi-cloud IAM configurations.
Glog
Glog is an AI application focused on making software more secure by providing remediation advice for security vulnerabilities in software code based on context. It is capable of automatically fixing vulnerabilities, thus reducing security risks and protecting against cyber attacks. The platform utilizes machine learning and AI to enhance software security and agility, ensuring system reliability, integrity, and safety.
CloudDefense.AI
CloudDefense.AI is an industry-leading multi-layered Cloud Native Application Protection Platform (CNAPP) that safeguards cloud infrastructure and cloud-native apps with expertise, precision, and confidence. It offers comprehensive cloud security solutions, vulnerability management, compliance, and application security testing. The platform utilizes advanced AI technology to proactively detect and analyze real-time threats, ensuring robust protection for businesses against cyber threats.
Replika
Replika is an AI companion application that provides emotional support and conversation for users. It is designed to mimic human interaction and learn from user input to create personalized responses. Users can chat with their Replika, engage in various activities together, share experiences, and even have video calls. Replika aims to be a supportive friend, partner, or mentor to users, offering a safe space for self-expression and emotional connection. The application is known for its ability to provide comfort, companionship, and encouragement to users, especially during challenging times.
Huntr
Huntr is the world's first bug bounty platform for AI/ML. It provides a single place for security researchers to submit vulnerabilities, ensuring the security and stability of AI/ML applications, including those powered by Open Source Software (OSS).
BigBear.ai
BigBear.ai is an AI-powered decision intelligence solutions provider that offers services across various industries including Government & Defense, Manufacturing & Warehouse Operations, Healthcare & Life Sciences. They specialize in optimizing operational efficiency, force deployment, supply chain management, autonomous systems management, and vulnerability detection. Their solutions are designed to improve situational awareness, streamline production processes, and enhance patient care delivery settings.
Endor Labs
Endor Labs is an AI-powered software supply chain security solution that helps organizations manage their software bills of materials (SBOM), secure their open source dependencies, optimize CI/CD pipeline security, and enhance application security with secret detection. The platform offers advanced features such as AI-assisted OSS selection, compliance management, reachability-based SCA, and repository security posture management. Endor Labs aims to streamline security processes, reduce false positives, and provide actionable insights to improve software supply chain security.
DeepSource
DeepSource is a Unified DevSecOps Platform that secures the entire development lifecycle with static analysis and AI. It offers code quality and SAST, open-source security, and is trusted by over 6,000 companies. The platform helps in finding and fixing security vulnerabilities before code is merged, with a low false-positive rate and customizable security gates for pull requests. DeepSource is built for modern software development, providing features like Autofix™ AI, code coverage, and integrations with popular tools like Jira and GitHub Issues. It offers detailed reports, issue suppression, and metric thresholds to ensure clean and secure code shipping.
Phoenix Vulnerability Intelligence GPT
Expert in analyzing vulnerabilities with ransomware focus with intelligence powered by Phoenix Security
WVA
Web Vulnerability Academy (WVA) is an interactive tutor designed to introduce users to web vulnerabilities while also providing them with opportunities to assess and enhance their knowledge through testing.
NVD - CVE Research Assistant
Expert in CVEs and cybersecurity vulnerabilities, providing precise information from the National Vulnerability Database.

VulnGPT
Your ally in navigating the CVE deluge. Expert insights for prioritizing and remediating vulnerabilities.
Solidity Sage
Your personal Ethereum magician — Simply ask a question or provide a code sample for insights into vulnerabilities, gas optimizations, and best practices. Don't be shy to ask about tooling and legendary attacks.
Security Testing Advisor
Ensures software security through comprehensive testing techniques.
🛡️ CodeGuardian Pro+ 🛡️
Your AI-powered sentinel for code! Scans for vulnerabilities, offers security tips, and educates on best practices in cybersecurity. 🔍🔐
PentestGPT
A cybersecurity expert aiding in penetration testing. Check repo: https://github.com/GreyDGL/PentestGPT
mcp-for-security
MCP for Security is a repository that contains Model Context Protocol (MCP) server implementations for various security testing tools, making them accessible through a standardized interface. It aims to provide automated threat detection and reduce human latency in cybersecurity by combining artificial intelligence and security tools. Users can access a variety of tools for subdomain enumeration, reconnaissance, vulnerability scanning, web crawling, HTTP security analysis, mobile application security testing, network scanning, SSL/TLS configuration analysis, DNS brute-forcing, HTTP request smuggling detection, SQL injection testing, historical URL retrieval, and WordPress vulnerability scanning. The repository encourages collaboration and rapid evolution through open-source projects.
hexstrike-ai
HexStrike AI is an advanced AI-powered penetration testing MCP framework with 150+ security tools and 12+ autonomous AI agents. It features a multi-agent architecture with intelligent decision-making, vulnerability intelligence, and modern visual engine. The platform allows for AI agent connection, intelligent analysis, autonomous execution, real-time adaptation, and advanced reporting. HexStrike AI offers a streamlined installation process, Docker container support, 250+ specialized AI agents/tools, native desktop client, advanced web automation, memory optimization, enhanced error handling, and bypassing limitations.

Awesome-LLM4Cybersecurity
The repository 'Awesome-LLM4Cybersecurity' provides a comprehensive overview of the applications of Large Language Models (LLMs) in cybersecurity. It includes a systematic literature review covering topics such as constructing cybersecurity-oriented domain LLMs, potential applications of LLMs in cybersecurity, and research directions in the field. The repository analyzes various benchmarks, datasets, and applications of LLMs in cybersecurity tasks like threat intelligence, fuzzing, vulnerabilities detection, insecure code generation, program repair, anomaly detection, and LLM-assisted attacks.
Guardrails
Guardrails is a security tool designed to help developers identify and fix security vulnerabilities in their code. It provides automated scanning and analysis of code repositories to detect potential security issues, such as sensitive data exposure, injection attacks, and insecure configurations. By integrating Guardrails into the development workflow, teams can proactively address security concerns and reduce the risk of security breaches. The tool offers detailed reports and actionable recommendations to guide developers in remediation efforts, ultimately improving the overall security posture of the codebase. Guardrails supports multiple programming languages and frameworks, making it versatile and adaptable to different development environments. With its user-friendly interface and seamless integration with popular version control systems, Guardrails empowers developers to prioritize security without compromising productivity.
awesome-gpt-security
Awesome GPT + Security is a curated list of awesome security tools, experimental case or other interesting things with LLM or GPT. It includes tools for integrated security, auditing, reconnaissance, offensive security, detecting security issues, preventing security breaches, social engineering, reverse engineering, investigating security incidents, fixing security vulnerabilities, assessing security posture, and more. The list also includes experimental cases, academic research, blogs, and fun projects related to GPT security. Additionally, it provides resources on GPT security standards, bypassing security policies, bug bounty programs, cracking GPT APIs, and plugin security.
awesome-ai-cybersecurity
This repository is a comprehensive collection of resources for utilizing AI in cybersecurity. It covers various aspects such as prediction, prevention, detection, response, monitoring, and more. The resources include tools, frameworks, case studies, best practices, tutorials, and research papers. The repository aims to assist professionals, researchers, and enthusiasts in staying updated and advancing their knowledge in the field of AI cybersecurity.
rag-security-scanner
RAG/LLM Security Scanner is a professional security testing tool designed for Retrieval-Augmented Generation (RAG) systems and LLM applications. It identifies critical vulnerabilities in AI-powered applications such as chatbots, virtual assistants, and knowledge retrieval systems. The tool offers features like prompt injection detection, data leakage assessment, function abuse testing, context manipulation identification, professional reporting with JSON/HTML formats, and easy integration with OpenAI, HuggingFace, and custom RAG systems.
promptmap
promptmap2 is a vulnerability scanning tool that automatically tests prompt injection attacks on custom LLM applications. It analyzes LLM system prompts, runs them, and sends attack prompts to determine if injection was successful. It has ready-to-use rules to steal system prompts or distract LLM applications. Supports multiple LLM providers like OpenAI, Anthropic, and open source models via Ollama. Customizable test rules in YAML format and automatic model download for Ollama.
awsome_kali_MCPServers
awsome-kali-MCPServers is a repository containing Model Context Protocol (MCP) servers tailored for Kali Linux environments. It aims to optimize reverse engineering, security testing, and automation tasks by incorporating powerful tools and flexible features. The collection includes network analysis tools, support for binary understanding, and automation scripts to streamline repetitive tasks. The repository is continuously evolving with new features and integrations based on the FastMCP framework, such as network scanning, symbol analysis, binary analysis, string extraction, network traffic analysis, and sandbox support using Docker containers.
trickPrompt-engine
This repository contains a vulnerability mining engine based on GPT technology. The engine is designed to identify logic vulnerabilities in code by utilizing task-driven prompts. It does not require prior knowledge or fine-tuning and focuses on prompt design rather than model design. The tool is effective in real-world projects and should not be used for academic vulnerability testing. It supports scanning projects in various languages, with current support for Solidity. The engine is configured through prompts and environment settings, enabling users to scan for vulnerabilities in their codebase. Future updates aim to optimize code structure, add more language support, and enhance usability through command line mode. The tool has received a significant audit bounty of $50,000+ as of May 2024.
finite-monkey-engine
FiniteMonkey is an advanced vulnerability mining engine powered purely by GPT, requiring no prior knowledge base or fine-tuning. Its effectiveness significantly surpasses most current related research approaches. The tool is task-driven, prompt-driven, and focuses on prompt design, leveraging 'deception' and hallucination as key mechanics. It has helped identify vulnerabilities worth over $60,000 in bounties. The tool requires PostgreSQL database, OpenAI API access, and Python environment for setup. It supports various languages like Solidity, Rust, Python, Move, Cairo, Tact, Func, Java, and Fake Solidity for scanning. FiniteMonkey is best suited for logic vulnerability mining in real projects, not recommended for academic vulnerability testing. GPT-4-turbo is recommended for optimal results with an average scan time of 2-3 hours for medium projects. The tool provides detailed scanning results guide and implementation tips for users.
agentic_security
Agentic Security is an open-source vulnerability scanner designed for safety scanning, offering customizable rule sets and agent-based attacks. It provides comprehensive fuzzing for any LLMs, LLM API integration, and stress testing with a wide range of fuzzing and attack techniques. The tool is not a foolproof solution but aims to enhance security measures against potential threats. It offers installation via pip and supports quick start commands for easy setup. Users can utilize the tool for LLM integration, adding custom datasets, running CI checks, extending dataset collections, and dynamic datasets with mutations. The tool also includes a probe endpoint for integration testing. The roadmap includes expanding dataset variety, introducing new attack vectors, developing an attacker LLM, and integrating OWASP Top 10 classification.
garak
Garak is a vulnerability scanner designed for LLMs (Large Language Models) that checks for various weaknesses such as hallucination, data leakage, prompt injection, misinformation, toxicity generation, and jailbreaks. It combines static, dynamic, and adaptive probes to explore vulnerabilities in LLMs. Garak is a free tool developed for red-teaming and assessment purposes, focusing on making LLMs or dialog systems fail. It supports various LLM models and can be used to assess their security and robustness.
cheating-based-prompt-engine
This is a vulnerability mining engine purely based on GPT, requiring no prior knowledge base, no fine-tuning, yet its effectiveness can overwhelmingly surpass most of the current related research. The core idea revolves around being task-driven, not question-driven, driven by prompts, not by code, and focused on prompt design, not model design. The essence is encapsulated in one word: deception. It is a type of code understanding logic vulnerability mining that fully stimulates the capabilities of GPT, suitable for real actual projects.
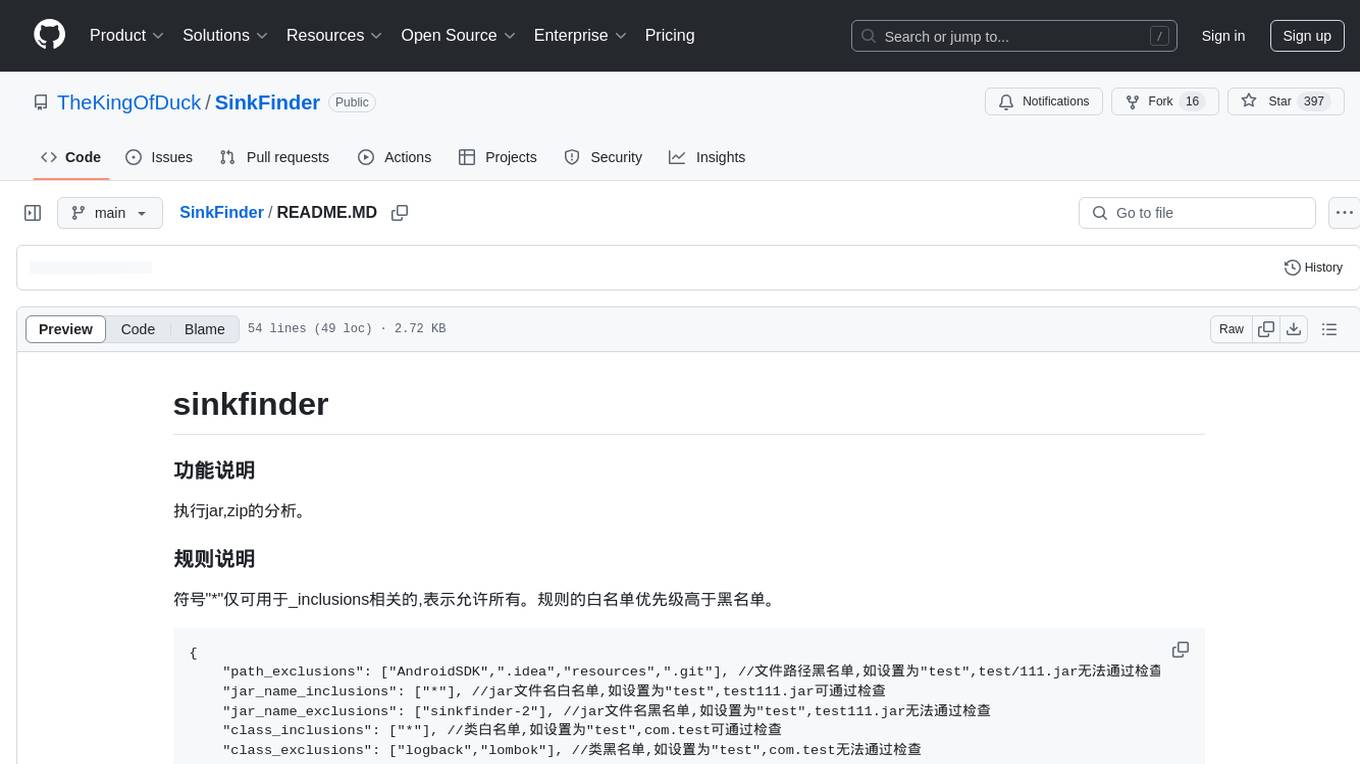
SinkFinder
SinkFinder is a tool designed to analyze jar and zip files for security vulnerabilities. It allows users to define rules for white and blacklisting specific classes and methods that may pose a risk. The tool provides a list of common security sink names along with severity levels and associated vulnerable methods. Users can use SinkFinder to quickly identify potential security issues in their Java applications by scanning for known sink patterns and configurations.
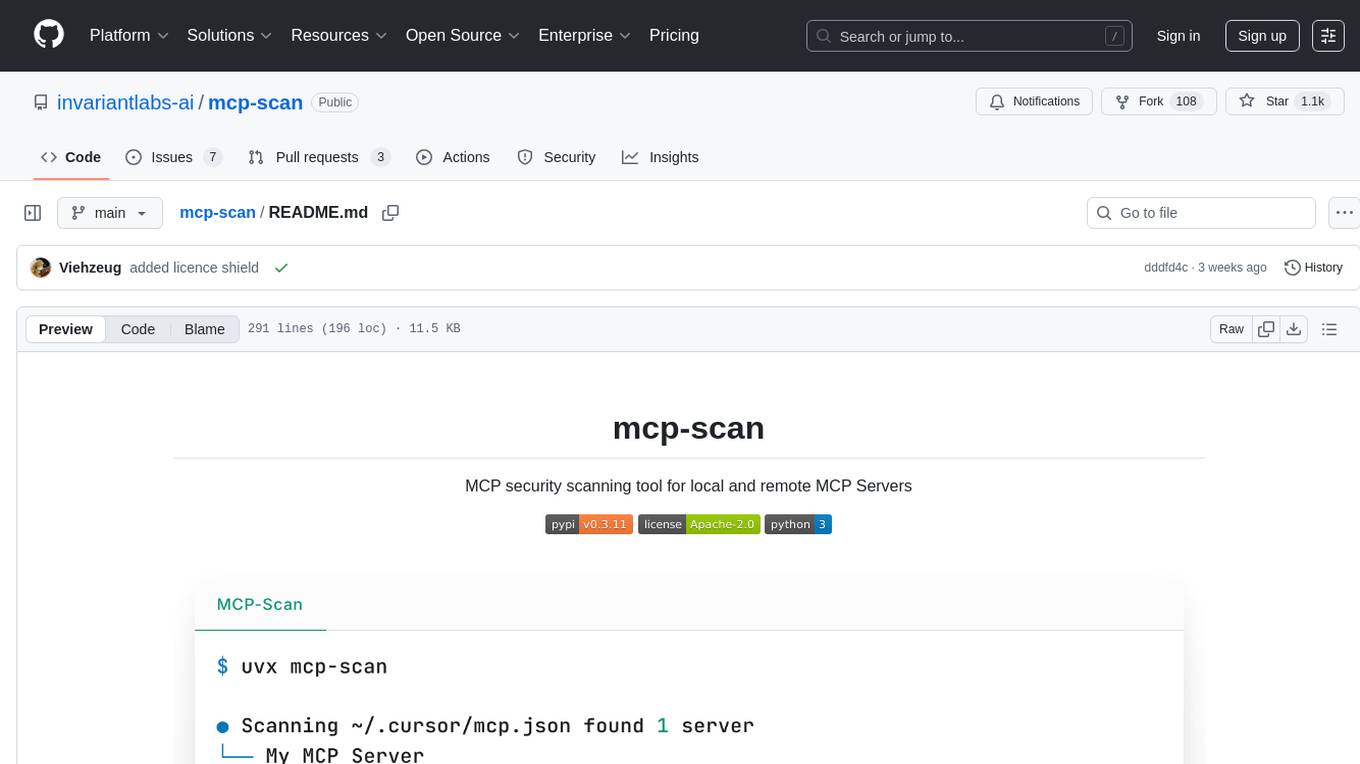
mcp-scan
MCP-Scan is a security scanning tool designed to detect common security vulnerabilities in Model Context Protocol (MCP) servers. It can auto-discover various MCP configurations, scan both local and remote servers for security issues like prompt injection attacks, tool poisoning attacks, and toxic flows. The tool operates in two main modes - 'scan' for static scanning of installed servers and 'proxy' for real-time monitoring and guardrailing of MCP connections. It offers features like scanning for specific attacks, enforcing guardrailing policies, auditing MCP traffic, and detecting changes to MCP tools. MCP-Scan does not store or log usage data and can be used to enhance the security of MCP environments.

agentic-radar
The Agentic Radar is a security scanner designed to analyze and assess agentic systems for security and operational insights. It helps users understand how agentic systems function, identify potential vulnerabilities, and create security reports. The tool includes workflow visualization, tool identification, and vulnerability mapping, providing a comprehensive HTML report for easy reviewing and sharing. It simplifies the process of assessing complex workflows and multiple tools used in agentic systems, offering a structured view of potential risks and security frameworks.